Do know evil – New Zealand in the age of Capital Surveillance.
Posted by vonnagy on Dec 27 2019, in Advertising, asylon, Capital Surveillance, Marketing, Media, new zealand, technology
About 15 years ago, I was both an avid amateur photographer and web developer. This naturally led me to build a website showing off my best photographs. It was a simple website that I cobbled together in part from an open source shopping cart system. The cart system had a ‘share this product’ feature which I converted into an ‘e-card’ system.
A year later I finally decided to back up my data, and I was surprised at the size of the database. Thinking the size was due to a bug, I browsed through my backup SQL file. There were thousands of personal messages in my database that used my e-card system. Out of curiosity, I began to browse through the messages. For the most part, they were short hellos, messages of love, and how much they would like visit New Zealand some day.
But in the midst of browsing through entries, I came across a note from a close friend of mine. The message discussed a private matter that was clearly intended for the recipient’s eyes, not mine. I felt ashamed about my voyeurism, wishing I had never read it, just as I would not want anyone to read my own personal messages. My e-card users did not understand privacy issues, and as a site owner, neither did I. Even though my janky e-card system proved popular, I decided to take it down.
Today this matter rings true for not only for most businesses, but entire industries. Its called surveillance capitalism. This type of capitalism profits by monitoring consumers. I gleans personal information from any device that is connected to the internet: whether it is your laptop, mobile phone or even your refrigerator. To make matters worse, it often leverages others businesses to provide this data, laundering the data trail to your personal information. It hinges upon us not knowing or caring about how it works. Upton Sinclair once said:
“It’s difficult to get a man to understand something when his salary depends on him not understanding it.”
This is my story of involvement with surveillance capitalism. It goes beyond my experience with my tiny photo website to one of the most successful internet startups in Zealand. Though this work was based in New Zealand, the tendrils of surveillance capitalism knows no boundaries. Much of this has been uncomfortable to write, because in doing so, it made realise that I was an accomplice to many of the subversive practices discussed here.
Table of Contents:
- Do know evil – New Zealand in the age of Capital Surveillance.
… maybe you shouldn’t be doing it in the first place.
Though technology-wise 2005 is a lifetime ago, it was the first time I saw a glimpse behind the ethos of the internet phenom Google. Google had blacklisted CNET reporters after reporting then CEO Eric Schmidt’s personal information, by using Google itself:
After the article appeared, David Krane, Googles director of public relations, called CNET editors to complain, said Jai Singh, the editor in chief of CNETNews.com. “They were unhappy about the fact we used Schmidt’s private information in our story,” Mr. Singh said. “Our view is what we published was all public information, and we actually used their own product to find it.”
Since then, it Schmidt changed his tune. On one hand he abhorred that others find out how much money he made (and where he lived, his donations etc), but just 4 years later he came up with this infamous quote that been oft repeated in many ways:
“If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
Conversely, are there things that Google should not have been doing in the first place? [1]
The same year Eric Schmidt blacklisted CNET, we also launched our start up. As typical for startups, I had multiple roles: programming, project management, human resources, search engine optimisation, and online advertising. The later role is one our company became really good at. So proud were we of our advertising prowess, we later spun off an advertising agency that displayed our efficient use of Google’s pay per click program:
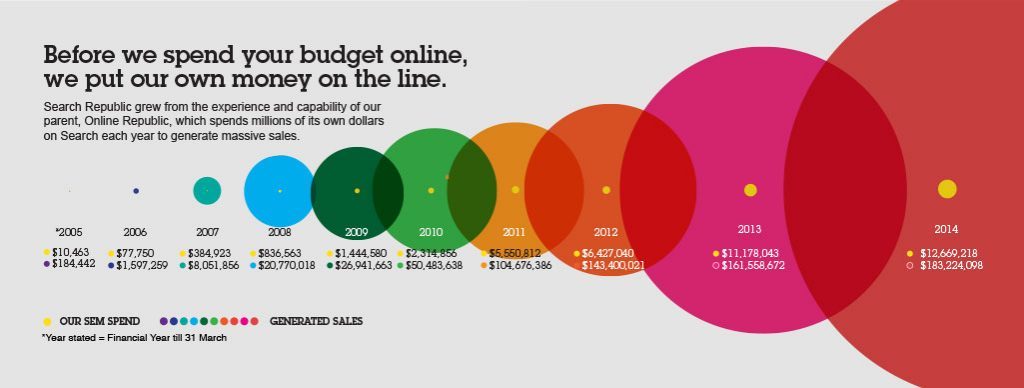
In the graphic above, our Adspend nearly doubled from 2012 to 2013. Why was this? We ran a multiple web site marketing strategy that was hit hard by Google algorithm updates in 2013, causing our organic (non-paid) traffic to plummet. Prior to the algorithm change, roughly 20-25% came from organic search. Immediately the algorithm change, it was around 3-5%. Making matters worse, the organic markets that were hit hardest were in our own backyard, New Zealand and Australia. We took a big chance by doubling our spend on Adwords.
Oddly enough, the same sites culled by Google as ‘spam’ did exceedingly well under Google paid ads. Google dominates the global search market both ends: through paid and organic (non-paid) search. From our business point of view, it made sense to acquire as many organic searches as possible.
I wasn’t just us, but nearly every algorithm in Google’s war on spam had collateral damage on private individuals and small businesses. [2] In 2013, we spent over $11 million dollars in Google advertising. That year, Google reported a $60,000 loss in New Zealand. [3]. Following this time, we saw many small businesses, particularly those who did not want to invest in Adwords, fall away to obscurity [4] or even go under. Our business could not survive without using the Google platform, there is no alternative. In the end, what could our company do? What could any New Zealand company do? What can any company in any country do where Google has more than 70% of the search market share?
Our attempts offset our exposure to Google’s dominance included an affiliate program and the aforementioned agency. The affiliate program targeted partners that did well in search engine optimisation (SEO), to make up for our own SEO losses. Our advertising agency used the strength of our in-house paid marketing. But regardless whether it was SEO from affiliates, or new clients from our agency, all roads lead to Mountain View.
In hindsight, it’s not just Google’s monopoly that bothers me. Our business contributed in feeding the the Google data beast. Every site we owned contained Google statistical tracking codes, whether from Analytics or Google Ads. We generated millions of dollars for Google, but we also generated millions upon millions of clicks, billions views and impressions. While this data useful to us, we could not connect our data to user. On the surface, this looks wonderful, businesses are cuffed when tracking their customers, and rightfully so. Business can also lean on Google to take care of privacy issues.
However, this leads to a blind spot: what does Google do with this collected data? We never see our data out of the bubble of our business. However, Google can connect the dots from our business to every point customer has been. Tools such Analytics, GoogleAds, TagManager enable Google to peer into users habits across entire industries in ways we could never imagine. It keeps them one step ahead of everyone, enabling Google to bring entire industries under their heel [5]. In fact Google, with its subtle chutzpah, requests that businesses upload its offline data for adwords, upload additional analytics data, and DataStudio.
In a particularly surreal moment for our business, a new Google account manager introduced themselves for our business verticals. They candidly remarked that they were not only our account manager but also managed our biggest competitor. Our account spent millions of New Zealand dollars per annum. They saw no conflict of interest in this, after all, it was just data to them. I’ll not forget the startled look on their face when we called them out on that. For a brief moment they considered our position, before towing the company line that all data was neutral. We eventually got a new account manager. [6]
Our business fed Google the countless sets of data, without batting an eye of what those consequences would be. But how did it get this way?
The Google Opacity Project – 3 examples of Google behaving badly.
How did Google become a monopoly? Under the shadow of night of fog:
Former ex-Googler Douglas Edwards writes compellingly about this predicament and the culture of secrecy it shaped. According to his account, Page and Brin were “hawks,” insisting on aggressive data capture and retention: “Larry opposed any path that would reveal our technological secrets or stir the privacy pot and endanger our ability to gather data.” Page wanted to avoid arousing users’ curiosity by minimizing their exposure to any clues about the reach of the firm’s data operations. He questioned the prudence of the electronic scroll in the reception lobby that displays a continuous stream of search queries, and he “tried to kill” the annual Google Zeitgeist conference that summarizes the year’s trends in search terms. [7]
Think about how all pervasive Google has become: your mail, maps, mobile, translations, and even your DNA is part of the Google empire. To get there, Google became a master of obfuscation. There hundreds (perhaps thousands) of Google’s abuse of data, many of these are highlighted in Shoshana Zuboff’s pièce de résistance “Age of Surveillance Capitalism” . [8]. I’ve only highlighted 3 examples here, which I’ve included to highlight both Google’s subtlety and outright brazenness on the quest to collect global data.
Maps & Streetview . Wardriving is using a vehicle to find unsecured or easily hacked wifi hotspots. Google, did not have internet access to many places to enable their map products. In many areas, Google tapped in private wifi routers to enable their mapping capabilities. Google recovered a lot of data from their quest to map the world.
Technical experts in Canada, France, and the Netherlands discovered that the payload data included names, telephone numbers, credit information, passwords, messages, e-mails, and chat transcripts, as well as records of online dating, pornography, browsing behavior, medical information, location data, photos, and video and audio files. They concluded that such data packets could be stitched together for a detailed profile of an identifiable person.
Though Google vigorously denied this type data collection, it had be found out they had specifically selected an internal engineer who was renown for his expertise in wardriving. [9]
The Google ToolBar – This may be a ‘blast from the past’ for many users. A few may remember when Microsoft Internet Explorer dominated the search market. The Google Toolbar was both a brilliant idea and a trojan horse. It allowed for users to search on Google without even going to Google website. During the early 2000s, Microsoft had over 95% of the browser marketshare, and Google piggybacked off Internet Explorers ubiquity.
The toolbar was hounded by privacy advocates, in particular Ben Edelman who did a full expose on the toolbar’s lack of privacy which included:
- The toolbar tracks user search terms, devices, and pageviews, even if another search engine was used!
- Its search toolbar was simple to install but nearly impossible to uninstall completely.
- In some cases it kept tracking users after it would be uninstalled.
While the toolbar may no longer be prominent, it no doubt left an impact. This leverage help raise Google profile, and just a few years later, Google launched their own browser which now has over 60% of global market share on all devices (compared to Microsoft woeful 2%). There can be know doubt they cut their teeth on data collection with the tool.
Google reCaptcha – What is so bad about a cute little button that asks if you are a robot? Google’s war on spam bots, actually captures your browsing information, such as what site you are on, your ip information where your browser moves and a screenshot of the entire web page [10] that you are on . Here are some other things to be aware of:
- reCaptcha started out as an open source university project, until it was bought by Google in 2009
- It is everywhere – like the Google toolbar, nearly every site implements it. It is trivial for developers to install.
- It can thwart your attempts at privacy; if you use a virtual private server or Tor, sites that use Cloudfare will use reCaptcha to authenticate you. While your IP may be masked, your browser signature is not.
- It is invasive of your privacy. For instance, if it is installed on sensitive site (such as medical, financial, or governmental organisation), Google will know you visited this.
- Sadly, its not as effective – its can has been overcome by bots and artificial intelligence, and 3rd Party services, as well as frustrating users.
The first example made a lot of news and the courts; its easy to how hacking routers is an invasion of privacy. The latter examples are much more subtle, as users openly embrace the technology guised to be a useful tool, but in essence, has ulterior motives.
Google’s influence and the art of data laundering.
Google has emboldened others to tap in to the data ‘free collection’ with hopes for a cashing in on user data. Here are some examples:
- Microsoft – Reeling from their loss of browser market, Microsoft CEO Satya Nadella sought to make Microsoft great again by collect data via search engine Bing, Skype, and Cortana. All of these have been plague with both security and privacy issues, including outsourced Chinese workers who were hired to listen to conversations.
- Amazon– Similar to Microsoft, Alex is being listened to by contractors. To make matters worse, the type of conversations are home related, where the sanctity of privacy should rule supreme.
- Samsung – A partner of Google for their Android operating system, they have come under flak for potential spying via their TVs and selling user’s smartphone data.
But on the internet, Google still rules supreme and it has spawned a hydra by proxy. By providing other businesses its own data collection tools (analytics, ads, captcha, tagmanager, datastudio). Google has created 1000’s of minions, each of which collect data for them. In particular, these are marketing companies who are looking trying to break big with their own consumer data niche.
To get an idea how much this market has grown, check out the Martech infographic. Visually it is staggering, looking closer to the million dollar home page project than a standard marketing infographic:

All these companies will likely use some type of Google tool to collect data for their systems. In a sense, the agents become data laundering service for Google, collect information that Google would never have considered before.
The above are marketing companies, but remember, entire industries use the same tools so the results get augmented over and over again. The breadth can be mesmerising; from business website builder Weebly injects analytics code by default on their web templates, to Wacom which installed analytics on their drawing tablets, to entire government sites using analytics.
Understanding Google’s digital priesthood. Privacy is easy, choice isn’t.
In 2017, Google generated 20 Petabytes of data day, which would mean roughly 6,798,655,000 Gigabytes of data per year. I am sure that number has grown since then. What does Google do with this data? In essence, your actions are the raw material to feed Google’s actual customers: the advertisers. In this sense, its not who you are you, its what you do. This becomes a very important distinction, because it sidesteps privacy issues:
- Google isn’t tracking users on Google Maps; its user’s behaviour on Google Maps
- Google isn’t tracking children on ChromeBooks; its tracking your behaviour on Chromebooks
- Its not users on Android; its users behaviour on Android
- Its not users on Fitbit; its how users use Fitbit
- It is not your DNA; its how your DNA connects to other people and drug manufacturing.
There hundreds other Google acquisitions to consider.
Data has become our modern God. It has been said in so many ways. Just as priests are the middle man between you and God, Google has the middle man for your data. Your email, your video watching habits, your searches, your dna, your movements. This means power for the new priests, and you must pass through them first. In this sense, Google become the intercessor, or priest of our data. The definition of a priest is one authorised as a mediatory agent between humans and God; Google is the intercessor between your data and those that have interest in it. Simply put, Google wants our know our habits. Our habits make us predictable. In the past centuries, we trusted priests to guide our behaviour based on holy scripts. Now, using petabyes of collected data, Google can drive guide behaviour.
Google realised early on that it would come across privacy issues. It has a very extensive privacy policy and its data protection, data anonymisation have been lauded.
Yet there is something missing here: your choice. When you are on the internet now, you are given little or no choice but to use Google products in some for or another. This is referred to decision rights. Shoshana Zuboff explains Google’s abuse of decision rights:
That Google had the power to choose secrecy is itself testament to the success of its own claims. This power is a crucial illustration of the difference between “decision rights” and “privacy.” Decision rights confer the power to choose whether to keep something secret or to share it. One can choose the degree of privacy or transparency for each situation… Surveillance capitalism lays claim to these decision rights…
Google discovered this necessary element of the new logic of accumulation: it must assert the rights to take the information upon which its success depends. Surveillance is the path to profit that overrides “we the people,” taking our decision rights without permission and even when we say “no.”..
The first stage of successful dispossession is initiated by unilateral incursion into undefended space: your laptop, your phone, a web page, the street where you live, an e-mail to your friend, your walk in the park, browsing online for a birthday gift, sharing photos of your kids, your interests and tastes, your digestion, your tears, your attention, your feelings, your face…
[This] Incursion moves down the road without looking left or right, continuously laying claim to decision rights over whatever is in its path. “I’m taking this,” it says. “These are mine now.”
Here we see the pattern:
- Google uses systematic obfuscation hiding behind technology to gain control.
- What they want is your behaviour, whether online or elsewhere. It is relentless pursuit of all the data that makes us human.
- Google has your data, you can not use partake in Google’s system without such collection.
- The Internet becomes Google.
Google has, and always will make claims, about your privacy. It will never sell your data, because that data is far too valuable to them. It will launch Privacy Awareness Weeks and have very slick videos that all your data is in safe hands. However, what choice did you have in the matter of giving your data away? Did you ask for Google to track your purchase history, your whereabouts on Google maps, health history, and your search history. Some of these have only been recently exposed. Other exposures have been done under subpoena or whistleblowers.
Finding Asylum
People don’t want to admit that propaganda works, because to admit it, means confronting own susceptibilities, horrific lack of privacy, and hopeless dependency on tech platforms ruining our democracies on various attack surfaces. David Carroll, The Great Hack.
As bleak as this may seem, the tide is turning. New Zealand as individuals and as a country can see what steps have been taken around the world. Some of them are big, some are small:
- In Europe, the General Data Protection Regulation is step for users to reclaim their data, and the right to be forgotten.
- California Consumer Privacy Act is the strongest privacy protection yet in the United States.
- Google’s own analytics are sagging, likely due to privacy plugins on browsers. A comparison of Google Analytics and a webserver log of this was written by the developer of Luapress. This is sign that users are becoming more savvy about their data protection.
- Innovations through the blockchain have made user data more private. Organisations such as Blockstack are working on building an decentralised online environment based on bitcoin where privacy is the norm. It includes similar free services such as email and documents. Time will tell if services such as these catch on.
- The ‘father’ of internet, Tim Berners-Lee as become appalled what the internet has become. His contract for the web outlines what can be done to make it better for everyone, including taking action against surveillance capitalism.
There is more that can be written, this article has already been worked on and tweaked for nearly 3 months. When this gets publish there may be things that changed.
One thing that has changed for certain is my outlook. I recently reviewed that old photo site I built. I winced when I noticed I actually had ‘default’ privacy policy which I did not adhere to. For the thousand or so people who used it to send messages, I sincerely apologise that I looked them, these have been deleted several years ago.
I would like conclude with another passage from Zuboff’s book:
The Greek word asylon means “unplunderable” and founds the notion of a sanctuary as an inviolable space.
Another translation is ‘unseizeable’ – from the suffix ‘a’ – without and ‘sylo’ -seize. It means sanctuary, and it is where we derive ‘asylum’ from. This has become of the namesake of this website.
My hope with this article (and this project) is that New Zealanders become more aware of the consequences of privacy, and do more to protect themselves and the ones they love. That is something that should never be seized.
Addendum: What you can do.
The sole worth of Google and Facebook is the fact that they possess and hold, and use the personal data of people from all around the world. So I think the best way to move forward are for people to really possess their data like their property. Brittany Kaiser, The Great Hack
Part of my own reflections was reduce (and hopefully altogether close) my own reliance on Google. Give how intertwined this data, its not an easy feat. My own online life is a work in progress. While there is no magic solution, here are some little things every New Zealander can do to step up your own privacy. The great news is that there are a lot of options, in fact this section is the longest of m
Easy (and little or no cost):
Tightening up your Social: There are a few things you can do to limit Google’s invasive reach into your data:
- Google Ads Opt Out
- Your Google Map History
- Youtube Search History
- Clear Google Purchase History
- Google TakeOut
Please note, that I said limit your expose. These are only items which Google acknowledges it holds on, in reality there could much more.
Also consider ways you secure your data from Facebook, Twitter, LinkedIn, Amazon and Netflix.
Understanding Fingerprinting. Your browser is likely to have a unique fingerprint, meaning advertisers can identify precisely who you are. Even if Google doesn’t have your name, it is likely that your browser can identify who you are 99% of time. There are several tools to combat this, but to get an idea of how this is done.
- Panopticlick by the Electronic Frontier Foundation
- Browser leaks
- Device Info
NoRoot Firewall / Disconnect.Me Apps for your mobile. Both of these can (and probably will) break your favourite mobile apps, but at least you will be able to see the outgoing data collections.
- NoRoot Firewall – Google Play
- Disconnect Me – Apple Store
Using Tor Browser – Tor is probably one best privacy tools on internet. Using a modified version of the Firefox browser, Your network connection is bounced between at least 3 connections globally – in a way that final connection can never know the originating source. It is inherently more secure than a VPN – which only offers a single point of failure, and where is Tor is essentially decentralised and trustless (that word sounds funny, but its opposite of you may think!)
Use Secure Messenger service. Signal and Telegram are both highly encrypted messenger services that you can use on your phone.
Whatsapp is secured by the mechanism that Signal uses, but it is owned by Facebook, and has become known for the hack on Jeff Bezos phone (which was not because the communication was insecure, but rather the attachment that was sent.)
Do not use Facebook messenger or Skype – these have inherent security and privacy issues.
Get rid of unwanted apps/programs – Tidy up your devices – if you are not using an app on your mobile phone, remove it. See also removing bloatware below.
Use a password manager – Beyond just your own security, some password managers also can report if you password has been involved in a data breach. As with everything do your research – many password managers are a single point of failure, meaning if they are breach, it gives access to all your passwords. So if you your password for your manager is ‘password’ or ‘abc123’, you are probably going to have a bad day. Use a good password manager.
Consider different search engines. I weaned my reliance on Google by switching to Duckduckgo, which I use about 70% of the time. Other search engines to consider include Qwant and Yippy.
If possible, try to stay logged out of Google search and Chrome browser if you use Google search. If you have a gmail account, try using an email client like Mozilla Thunderbird. This way you can at least be logged out of Google while you search, but still access your gmail.
Easy (some costs involved):
Faraday Bags and Boxes. Your smart phone is constantly signalling the carrier . Faraday bags and boxes block.
Consider a private email service. ProtonMail, Mailfence, and Tutanota are all advocates of privacy. If possible set up your own mail server. In either case, though won’t get slick cartoons about data collection on your terms and conditions, but at least you’ll get peace of mine about your privacy. Well less featured than Gmail, many times they offer a free service and paid service.
Gmail will track your purchases. While this may be convenient for some, the reality is that a profile of your spending habits is likely to be used for future Google Ads. If you do make purchases, consider using another email address.
VPN Use – This allows you to surf the internet on another IP. The internet is swarming with VPN providers, some are more anonymous than others. Do you research here.
Personal data removal service. There are several of these services, these are professionals who scour the internet for your information and help you delete or remove information. And example would Privacyduck.com. Ultimately, your data should your responsibility. However, if you have an exceptionally large online footprint and poor record keeping, it might be worth the money.
More Effort Required
Educate yourself on Privacy. Ask yourself what information you would like people to know (or not know) about you, and check and see how secure they are. Here are some thoughts about commonly used applications:
- What would Netflix know about you that you wouldn’t tell others?
- What does Steam know about you after playing over 1000 hours playing Skyrim?
- Will 23andMe reveal unwanted family history?
- Would it be easy to track my GPS coordinates from Fitbit?
- Would you open to complain about your company on Slack?
If the terms and conditions are convoluted, or it says it may share data with 3rd parties, it might be time to upgrade your privacy.
Firewalls – For any device you have, consider using a fire wall. For instance if you do not want a program (Google, Adobe, Steam, Cortana) reporting back on your behaviour. This may break the behaviour of the system.
Tails OS – Tails OS is a free, USB operating system that anonymises your online experience through tor, and also doesn’t save any data. This requires more effort because you have to create the USB yourself and get familiar with a new operating system. However, you do not have to install it. It is a fascinating project, and one that helped former Intelligence Community Systems Adminstrator Edward Snowden escape scrutiny while he reported on citizen privacy voilations. NSA has reported that use of Tails with the Tor browser was the biggest hindrance to their global Survelliance programme.
Get rid of Bloatware – I wish this was any easy step, but getting rid of bloatware – unwanted programs that are preinstalled on your device, can actually be complicated proccess. Not only may they stream out data on your actions, but also clog up system performance. Both Android and Windows can be bad, but there are plenty of tutorials on how to reduce difficult to remove programs. For Windows 10 Laptops and computers, Windows10Debloater is a good start. It does require some work, but it will take away unwante windows programs and help tame Cortana. For Android, here is an article that aids in removing bloatware: https://www.androidpit.com/how-to-uninstall-preinstalled-android-apps
Consider Another Operating System: While I know changing from Mac or Windows is tantamount to changing religions, the experience needn’t be that difficult. Personally Linux Mint is very easy learning curve, but there are many other ones that may suite your taste. You don’t even have to abandon your favourite Windows or Mac Programs, with compatibility software layers such as Wine and Darling. This is not for everyone, but considering you’ve already made it past 2,000 words, you are probably considering all options!
Reducing smart phone time. You’ve read this far? Take a breather. It this article should still be here when you get back.
Consider non Android/IOS phone. There are other operating systems for Smartphones, which may mean a learning curve. There are several already in the marketplace, and there has been alot of talk about the Librem 5. Other devices such as Necuno use Voice over IP instead of cellular modem [cellular modem problems], and the Betrusted – a device that acts as a middle man between your mobile and communications.
Considerable Effort
Below will require considerable effort – though not all of it is technical, but making conscious choices to change behaviour. I am still working through many of these points myself; while the concepts are simple, in practice it becomes much more difficult.
Quitting Social Media: This has been much talked about, and is large of scope to be written about here. The hardest part of quitting is that everyone else is one it as well. Consider incremental steps and studying how your data is used. The more you know how it affects your asylon, the easier it becomes to break free.
Dropping Gmail/Free Email Service – For some people, this will be as difficult than social media. There may be Gigabytes of data store on your drive and going through 500,000 emails is a daunting task. But it can be done.
Get a burner phone – You smart phone is always transmitting. A brick mobile has advantages in that the battery can be moved more easily and there are very fewer apps that report back to central servers about your habits.
Root your Mobile (Android Users)– No that kind of root, but gain administrative access (know as root). Rooting your Android will give you more control over your phone, but may also ruin the functionality of your phone. (I have not tried this with my device)
MicroG Project for Android – Though MicroG is still in Alpha software version, this is an alternative library for Google Play, Maps and network connections. At this stage its more for advanced users. I have not done this yet, but it something I will investigate.
Learn the technology – Set up your own mail server or file server. Set up a VPS for tor relay or an onion site. Learn to build your own Faraday box, create a Tails USB disk. Be curious about possibilities, instead of fearful or resigned. Learn about XKeyscore and New Zealand’s involvement with the Five Eyes. If you find privacy interesting, then it makes all the above much easier to learn. Be the persons that loves the learning as much as they love using the technology.
Be that girl (or guy) – If you see online company that violates privacy, do not be silent. Often times, business leaders don’t know what is implemented on their websites. Marketers and programmers will implement what is easy; Google products are optimised for ease of configuration, at the cost of privacy. There is no doubt some business leaders and government officials will roll their eyes, but ethical leaders will take these requests seriously. This requires a minimum of knowledge of technology, but does require an effort to go against complacency.
Footnotes
[1] Mozilla Firefox advocate Asa Dozler said the following about Eric Schmidt’s nothing hide speech:
That was Eric Schmidt, the CEO of Google, telling you exactly what he thinks about your privacy. There is no ambiguity, no “out of context” here…. And here’s how you can easily switch Firefox’s search from Google to Bing. (Yes, Bing does have a better privacy policy than Google.)
[2] Here is a comprehensive history of Google Algorithm updates: https://www.searchenginejournal.com/google-algorithm-history/. There are numerous articles about the collateral damage of their search algorithms. Here a couple:
- https://indivigital.com/news/you-destroyed-my-business-webmasters-and-seos-react-to-googles-latest-algorithmic-update/
- https://www.webentangled.com/brands-that-were-destroyed-due-to-google-search-algorithm-updates/
[3] It is hard to imagine them making a loss. Going forward, its likely that Online Republic will have spent over $100,000,000NZD on Adwords by 2020. Though Online Republic an international business, a large chunk of the revenue were from New Zealand customers, even if they represented a lower volume of sales. We know that our local partners and competitors also shelled out big money for paid ads as well – if you paid $1.00 for a click and they appear above you, they pay the same or more. Aside from the Tourism vertical, I imagine home grown successes Trademe.co.nz and the New Zealand real estate sector also contribute a huge amount to the local economy. Here are the links to financial statements from Google New Zealand from the companies office.These documents are all available to the public. I highlighted the “Total comprehensive income/loss for the year”, but I am not a forensic accountant. I imagine any spend that is Ad-generated falls under international. Have a look for yourself.
- 2018 1,037,915 NZD Loss
- 2017 -1,013,658 NZD Loss
- 2016 -603,755 NZD Loss
- 2015 -601,463 NZD Loss
- 2014 160,253 NZD Income
- 2013 -60,389 NZD Loss.
- 2012 – 52235 NZD Loss.
- 2011 -45089 NZD Loss.
- 2010 – 201692 NZD Loss.
Taxation has been controversial for Google. They were renown for their ‘Double Irish With A Dutch Sandwich’ tax strategy. This tax strategy was recently abandoned due to more relaxed tax laws in the United States.
As of writing this, Facebook is getting sued for 9 Billion USD the the US IRS for using Ireland as tax haven. Will IRD take notes or continue to accept tax losses from these data giants? It be certainly be interesting to find out whether or not revenue agencies have some bite or remain toothless against these behemoths.
As mentioned, I am not a tax specialist, so please do your own research and inquiries. I do know there is difference between tax avoidance and tax evasion, but that line is blurry for many of us.
[4] There is a popular joke amongst SEO practitioners: Where is the best place to hide a body? The second page of Google.
[5] Almost 10 years ago, our business went to a Google Travel Conference in Sydney. Here they unveiled the Google Flights, which aggregated flight data. Keep in mind, the invitees to the conference where flight agreggators that Google could destroy with this tool! The assured us they were the good guys during this conference. Expedia shortly find out Google is more than happy to break their promises. Is this type of disruption good for the businesses?
[6] A part of that difficulty is also knowing that my contacts at Google were some of the smartest and most genuine people that I have had the privilege of working with. My sincere wish is that the focus should be on corporate practices, not individuals.
[7] I’m Feeling Lucky): The Confessions of Google Employee Number 59, written in 2011, is a book by Douglas Edwards, Google’s first director of marketing and brand management. Here is an interesting review of this book by the late Aaron Schwartz:
There were many, many times in this book that I couldn’t help but wonder: How did he get away with writing this? Google apparently approved of the project and had chaperones in all his interviews, but nonetheless the book is just full of revelations and shockers that it’s hard to imagine Google would ever want to see the light of day..
[8] It goes without saying I am indebted to Shoshanna’s book, Age of Surveillance Capitalism for this article. On a personal note, the book itself help me put my own involvement with surveillance capitalism in perspective.
[9] See page 142-3, Age of Capital Surveillance:
The FCC found evidence that contradicted Google’s scapegoating narrative. The records showed that the engineer had e-mailed links to his software documentation to project leaders, who then shared them with the entire Street View team. It also found evidence that on at least two occasions, the engineer told his colleagues that Street View was collecting personal data. Despite these facts along with evidence of the company’s exhaustive internal software reviews and testing procedures and the regular transfer of payload data from Street View’s hard disks to Google’s Oregon data center, Google’s engineers denied any knowledge of personal data collection
[10] Regarding screen captures, here is an example of how the browser canvas tag can build up a screenshot of page, element by element. In addition, the screen capturing is already used Google in their feedback tool.